Reverse Proxy as a hidden guardian of hosting security and performance
Modern websites and web applications face security, efficiency, and traffic challenges. A reverse proxy is key infrastructure that solves these problems by acting as a silent guardian of security and performance.
In this article, we'll explore the inner workings of a reverse proxy, its benefits, and its increasing importance in web technology.
Reverse Proxy Basics
A reverse proxy is a mediator between clients and servers. Instead of clients contacting the server directly, they send their requests to the reverse proxy. The reverse proxy then forwards these requests to the appropriate server. This method enables the reverse proxy to perform a variety of functions, ranging from load balancing to security.
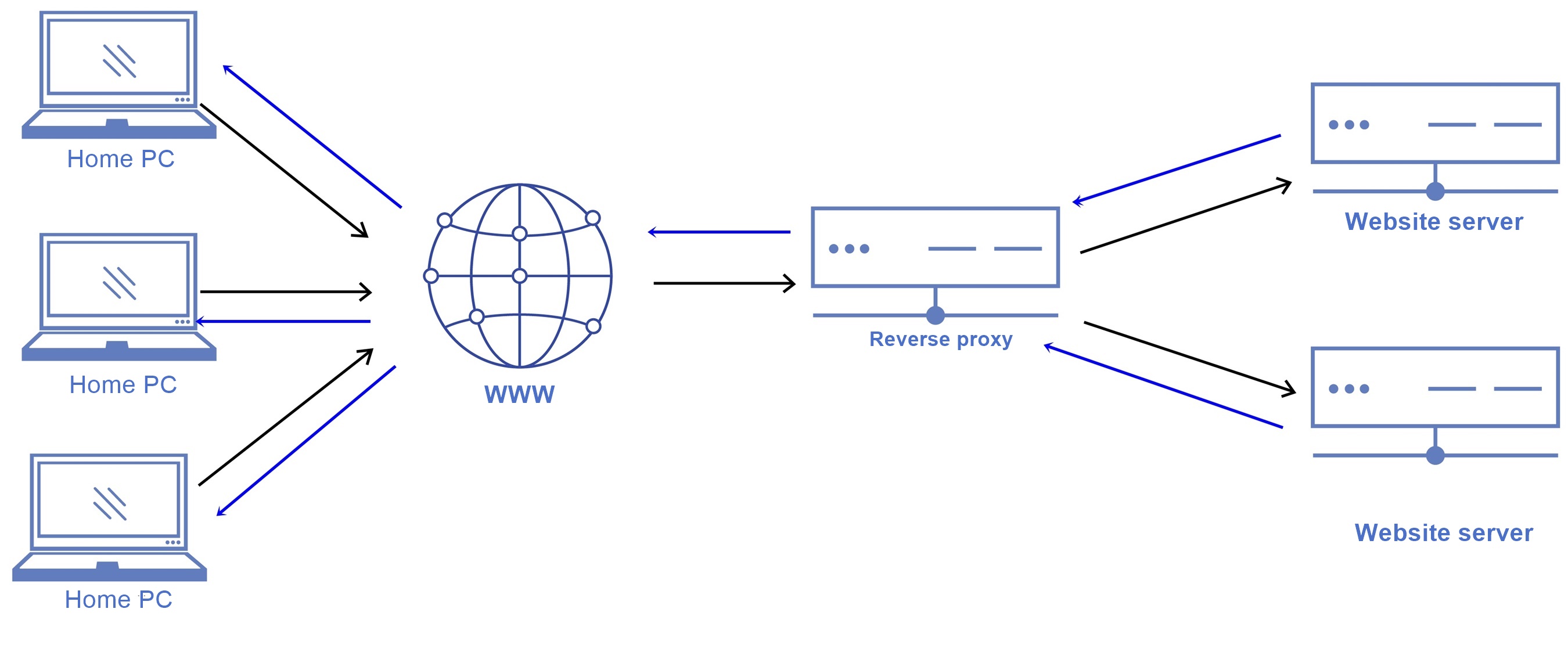
Load Balancing
Load balancing is a crucial feature of a reverse proxy. It helps to distribute incoming traffic among multiple servers, ensuring the optimal utilization of resources and preventing individual nodes from becoming overloaded. This operation is carried out by algorithms that assess the current server load and decide which server to route a new request to.
Load balancing is an effective technique used by reverse proxies to evenly distribute requests by dynamically adapting to changes in load. The algorithms used for load balancing can be as simple as circle distribution or more complex ones that consider factors such as server performance and geographical location.
Reverse proxy load balancing provides faster access to resources, especially in high-traffic environments or when the load needs to be distributed across remote servers.
Besides, load balancing plays a crucial role in enhancing the resilience of a system. When one of the servers fails, the reverse proxy automatically redirects the traffic to the operational nodes. This minimizes the downtime and ensures uninterrupted functioning of the web application. Administrators can set up load balancing based on different parameters such as server weights, performance, or availability. This helps optimize resource usage as per the specific requirements of a web application.
Caching for faster downloads
Caching is a process of storing copies of frequently requested static resources directly on the reverse proxy server. The reverse proxy server can decide which resources should be cached and set rules for updating the cache. This helps to keep the latest versions of static files in the cache, reducing the need to frequently contact the server for the same data.
Caching significantly reduces the response time of a website. This is because clients can obtain the requested resources from the cache of a reverse proxy. Apart from speeding up loading times, caching can also reduce the load on the server. This is because caching helps in saving resources by not processing repeated requests for the same static resources. This promotes more efficient use of server computing power.
It's important to note that a reverse proxy can also provide caching capabilities at different levels, including caching at the page or page fragment level. This enables configuring caching to suit the requirements of a specific web application.
Ensuring security
A reverse proxy is integral in securing web applications, starting with filtering traffic. It analyzes incoming requests and filters potentially dangerous or malicious requests, preventing them from being forwarded to the server. This action becomes a barrier to many types of attacks, such as SQL injection or cross-site scripting.
Resisting DDoS (Distributed Denial of Service) attacks is another important feature of a reverse proxy. By distributing incoming traffic across different servers, a reverse proxy reduces the likelihood of a successful DDoS attack and ensures the stability of the web application even under heavy traffic conditions. SSL termination, or decoding of SSL encryption on the reverse proxy side, provides an additional layer of security.
A reverse proxy can decrypt encrypted traffic, thereby providing a wider ability to inspect the content of requests and responses and enabling the identification of potential threats, control the security of transmitted data, and ensure confidentiality between customers and servers.
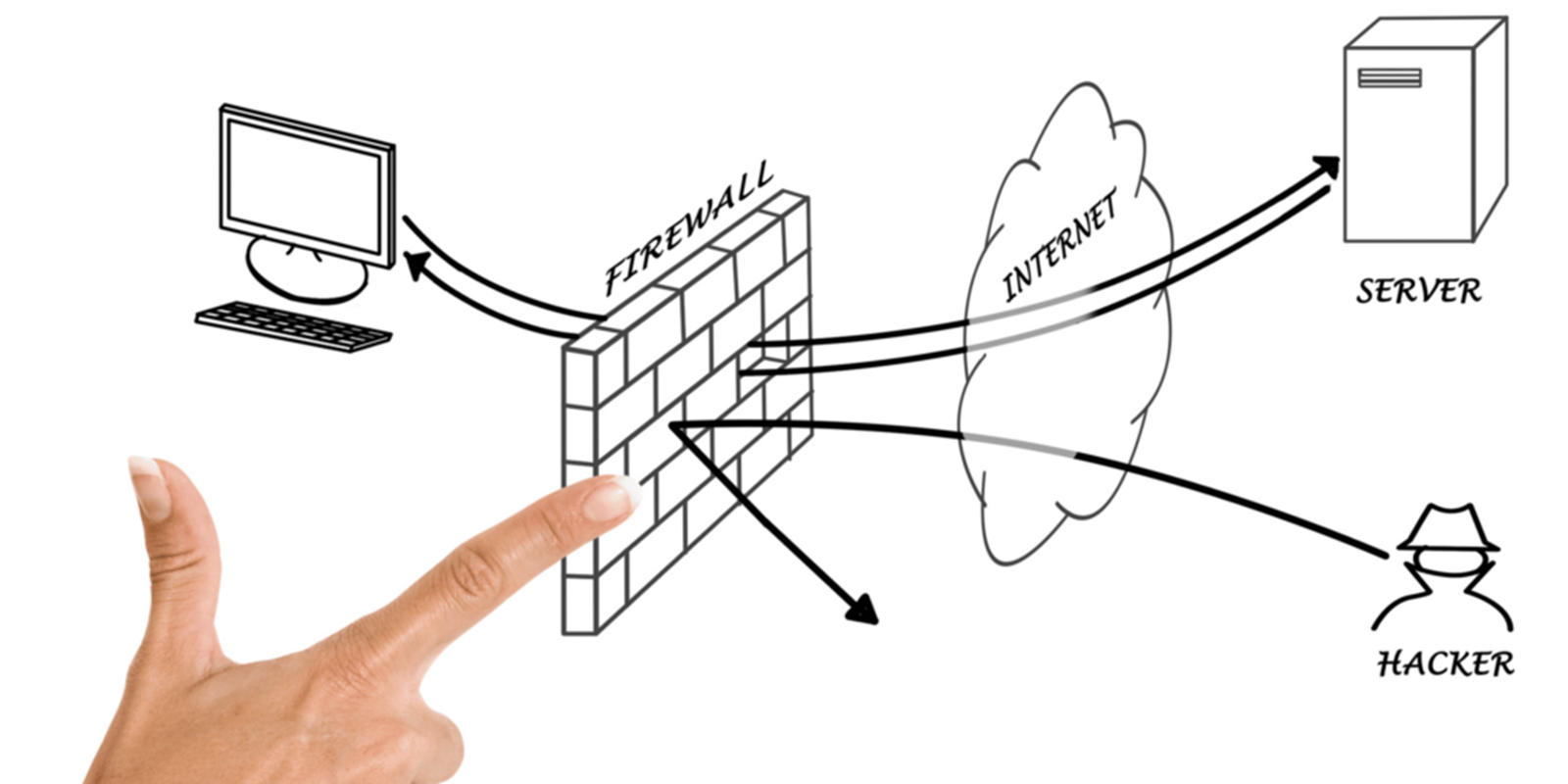
Moreover, a reverse proxy can serve as a content filtering role, blocking access to malicious web resources or inappropriate content. These filters help prevent application-level attacks and provide a means of controlling access to the website.
Masking the server architecture (this is exactly our product)
A reverse proxy provides camouflage to the server's architecture by providing clients with only their address instead of the server's real address. This is achieved by passing requests from clients to the server on behalf of a reverse proxy and returning responses from the server to the client through the proxy. In doing so, the actual characteristics of the server are inaccessible to end users, which increases the level of privacy and security.
Using this technique, you can also hide the internal network structure and server topology from the outside world. When a client accesses a web application through a reverse proxy, it sees only the proxy as an entry point, without revealing details of the location and characteristics of the actual servers. This hardens potential attackers to analyze the system and reduces the likelihood of successful attacks.
Masking the server architecture through a reverse proxy provides an additional layer of protection against targeted attacks such as port scanning and collection of server configuration information. Attackers face borders when identifying real hosts, which complicates attempts to exploit vulnerabilities.
Less information about the physical structure of the network is followed by additional difficulties for fraudsters in forming targeted attacks, which increases the level of protection of the web infrastructure.
Logging and monitoring (we do not keep logs)
The logging and monitoring provided by a reverse proxy are indispensable for effectively managing a web application or website.
Reverse proxy logs contain a deep set of data, ranging from request and response information to performance and security information, giving administrators a comprehensive overview of system performance. Reverse proxy logs provide detailed information about requests, including URLs, HTTP methods used, and request parameters. This provides complete context for how customers interact with the site, which can be used to analyze user behavior and identify potential problems.
Performance data like response time, latency, and resource load times are also recorded in the logs. This information allows administrators to identify site bottlenecks and take action to optimize performance, which is important to ensure a smooth and responsive user experience.
Reverse proxy logs include security data, like records of malicious requests detected or attack attempts, making them a valuable security monitoring tool. This information can be used to quickly respond to incidents and take action to eliminate potential threats.
Integrated monitoring tools based on reverse proxy logs provide real-time data visualization and analysis. This facilitates rapid response to changes in traffic, performance anomalies and security issues.
Thus, being a stealthy security and performance guardian, a reverse proxy is highly important in to-date web technologies. By understanding how it works and looking at its various features, we can understand why its implementation is becoming an increasingly integral element in the development and maintenance of websites and web applications.



